A Modchip To Root Starlink User Terminals Through Voltage Glitching
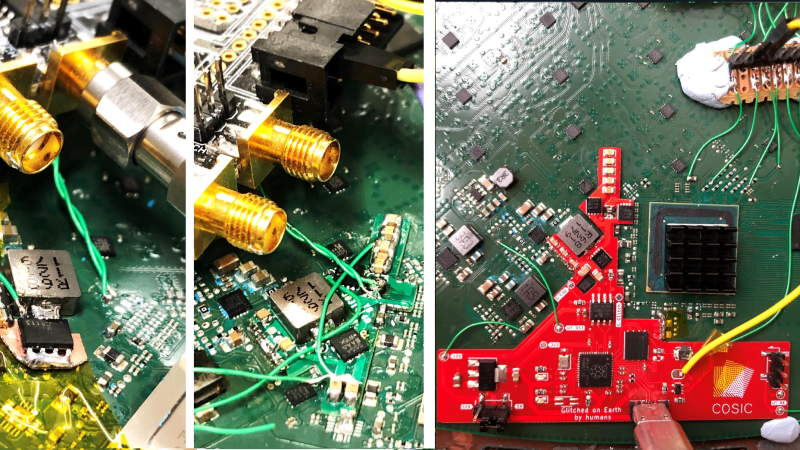
A modchip is a small PCB that mounts directly on a larger board, tapping into points on that board to make it do something it wasn’t meant to do. We’ve typically seen modchips used with gaming consoles of yore, bypassing DRM protections in a way that a software hacks couldn’t quite do. As software complexity and therefore attack surface increased on newer consoles, software hacks have taken the stage. However, on more integrated pieces of hardware, we’ll still want to return to the old methods – and that’s what this modchip-based hack of a Starlink terminal brings us.
[Lennert Wouters]’ team has been poking and prodding at the Starlink User Terminal, trying to get root access, and needed to bypass the ARM Trusted Firmware boot-time integrity checks. The terminal’s PCB is satellite-dish-sized, so things like laser fault injection are hard to set up – hence, they went the voltage injection route. Much poking and prodding later, they developed a way to reliably glitch the CPU into verifying a faulty firmware, and got to a root shell – the journey described in a BlackHat talk embedded below.
To make the hack more compact, repeatable and cheap, they decided to move it from a mess of wires and boards into slim form-factor, and that’s where the modchip design was made. For that, they put the terminal PCB into a scanner, traced a board outline out, loaded it into KiCad, and put all the necessary voltage glitching and monitoring parts on a single board, driven by the venerable RP2040 – this board has everything you’d need if you wanted to get root on the Starlink User Terminal. Thanks to the modchip design’s flexibility, when Starlink released a firmware update disabling the UART output used for monitoring, they could easily re-route the signal to an eMMC data line instead. Currently, the KiCad source files aren’t available, but there’s Gerber and BOM files on GitHub in case we want to make our own!
Hacks like these, undoubtedly, set a new bar for what we can achieve while bypassing security protections. Hackers have been designing all kinds of modchips, for both proprietary and open tech – we’ve seen one that lets you use third-party filters in your “smart” air purifier, another that lets you use your own filament with certain 3D printers, but there’s also one that lets you add a ton of games to an ArduBoy. With RP2040 in particular, just this year we’ve seen used to build a Nintendo 64 flash cart, a PlayStation 1 memory card, and a mod that adds homebrew support to a GameCube. If you were looking to build hardware addons that improve upon tech you use, whether by removing protections or adding features, there’s no better time than nowadays!
Post a Comment