RollBack Breaks Into Your Car
Rolling codes change the signal sent by car keyfobs unpredictably on every use, rendering them safe from replay attacks, and we can all sleep well at night. A research team lead by [Levente Csikor] gave a presentation at Black Hat where they disclose that the situation is not pretty at all (PDF).
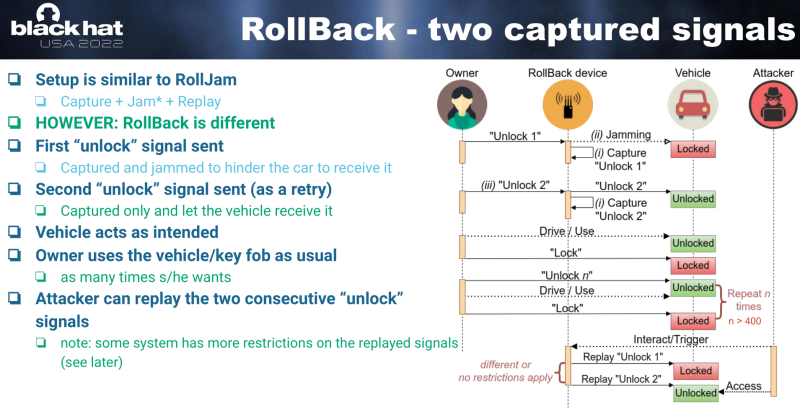
You might know [Samy Kamkar]’s RollJam attack, which basically consists of jamming the transmission between fob and car while the owner walks away, fooling the owner into clicking again, and then using one of the two rolling codes to lock up the car, keeping the other in your back pocket to steal it once they’re getting coffee. This is like that, but much, much worse.
It seems that most of the rolling-key systems accept a sequence of valid keys as kind of a “resync” code – the actual number varies from a sequence of two to five. RollBack, as the new hack is called, takes advantage of this behavior. You somehow eavesdrop on a few keyfob presses in a row, and you can reset the code and open the car forevermore. As with RollJam, probably the easiest way to get multiple codes from a fob is to jam a couple and record them all, but the jamming isn’t even necessary. Simply having a handful of consecutive keycodes suffices.
This “resync” behavior does seem to be documented in the rolling-code chips’ datasheets, as the researchers point out in their slides. In hindsight, it’s a horrendous security hole. Having a series of keyfob codes compromises a car forever, in contrast to [Samy]’s RollJam attack, which must be executed before the owner presses the fob again. We never got the details on a couple of prior claimed attacks, but it’s quite possible that this is what was going on.
If this flaw is as widespread as the researchers fear it is, we would be very careful about pressing our keyfob twice, because mitigation is going to be a nightmare.
Post a Comment